Class "A" License 15040139
Why choose Sleek Communications, Inc.?
We have been in business in the same location in Brookhaven, Mississippi since 1999. With over 35 years experience in communications and technology Sleek Communications, Inc. professional staff is well equipped to provide quality professional technology services for your business. We take great pride in our work and delivering to the customer solutions that fit any size project and budget. At Sleekcom we make technology work for you; not you work for technology.
Sleekcom Items Of Interest
Janurary 31, 2020
New Services Offered
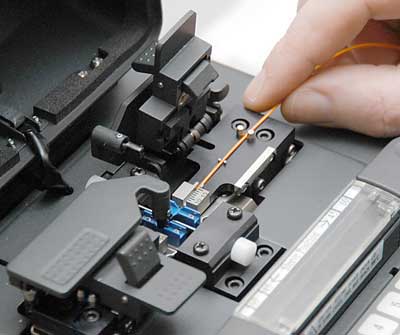
Fiber Optic Cable Fusion Splicing and Testing
Sleek Communications is excited to announce we are now fully equipped to perform fiber optic cable fusion splicing. Fusion splicing eliminates the need for mechanical terminations providing percision, reliable low-loss connections. Fusion splicing is more cost effective eliminating the need for costly mechanical connectors. Fusion splicing also allows for repair of fiber optic cable as well as economical extension and relocates compared to replacing an entire cable run.
Our precision equipment allows us to fusion splice nearly every type of fiber optic cable; SM, MM, DS and NZDS with minimal loss for each type. Our equipment also provides for a splice loss report to be delivered for each splice completed.
Once all fiber fusion splicing is complete our N.I.S.T. tracable test equipment can test and certify each fiber connection and provide a detailed report of each run.

March 4, 2016
Encryption Virus
Feburary 23, 2016
Phone Scam
If you receive a phone call from someone claiming to be with Windows or Microsoft stating they have recorded unusual activity from your computer, hang up. These scammers will request access to your computer by getting you to visit a website and download remote access software. Of course the prices they quote for "cleaning" your computer range anywhere from $90 to $400. Once you give them access to your computer, within seconds they have access to any personal or private information you many have stored on your computer. We had a customer come in recently that had their identity, medical records and personal information stolen in this manner. Unless you know the person or company you are dealing with NEVER, under any circumstances, download software they request you to or give them any information.
Sleek Communications services all brands and types of computers. Give us a call and let us help you get your machine back running smoothly, safely and speedy.